







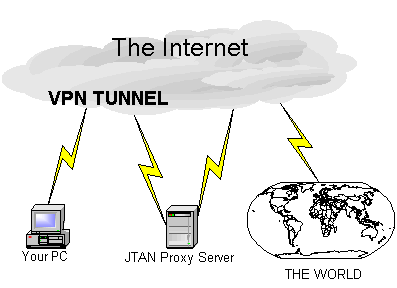
Using Tunnels for Privacy and JTAN Service Access
Another term for a tunnel is a "Virtual Private Network" or VPN. The idea is that your network connection disappears into the tunnel and then reappears here at JTAN as if you were directly connected. You are then "Virtually" connected to our local "Private Network".A VPN Tunnel to JTAN is useful for enhancing your privacy, facilitating the transport of multiple services through firewalls, and accessing services restricted to JTAN local hosts such as
- WWW Proxy
- NNTP Usenet News
- SMTP Relay
A key benefit to using a secure VPN Tunnel is that all your network activity is encrypted and funneled through a single network connection to a single port. This makes your activity both difficult to snoop, and easier to thread through a narrow hole in a firewall or router. Of course, once your traffic leaves the tunnel, it travels through the net in the normal way.
There two basic sorts of VPN Tunnels that JTAN supports: SSH port forwarding, and OpenVPN. The following sections show how to set them up.
SSH Port Forwarding
If you have a JTAN ProShell or ProWeb account, you have shell access to a JTAN host. With that access comes the ability to create a VPN tunnel using SSH port forwarding. SSH tunnels are handy for tunnelling a few kinds of traffic, say just your email and web browsing.The SSH protocol has the ability to forward arbitrary network connections to specific ports over your encrypted SSH connection to the JTAN shell machine. For example, you could use an SSH tunnel to connect from your home computer to the WWW proxy server at JTAN. Even if your company's firewall blocks SSH, there are tricks you can use to get around this.
In order to use SSH port forwarding to connect from your local machine to a port on a remote server, you need to:
- Choose a port number on your PC for your local end of the tunnel.
- Select the host address and port that you want to connect the other end of the tunnel to.
- Configure your SSH client to create a Local forwarded port between your local port and the remote host and port.
- Configure network applications on your PC to use "localhost" and the local port to access the service you are tunneling.
- Log in with SSH and use the tunnel.
SSH Applications
There are SSH applications for every OS. See the JTAN SSH Resource Page for details. Most of these applications do port tunneling, but not all, so choose carefully.Tunneling Using OpenSSH (Mac or Linux)
Here's typical OpenSSH comand for creating tunnels. To create a handy desktop icon that runs the command, you can wrap it with an xterm -e, or put it in a shell script that runs in a terminal.
ssh -Y -L 3128:webproxy.jtan.com:3128 [email protected]
The above example local tunnels to the webproxy. The -Y switch sets
up forwarding for Xwindows applications running on ganymede.
Tunneling Using Putty (Windoze)
PuTTY is probably the most popular SSH application that people use on Microsoft Windoze PC's. The capability to create VPN tunnels has been recently added (version 0.53 has it). The PuTTY User's Manual has a good discussion of Port Forwarding here. With PuTTY, before you start your SSH connection, be sure to go to
the Tunnels panel (see section
4.19.2 of the manual). Make sure the "Local" radio button
is set. Enter the local port number into the "Source port"
box. Enter the destination host name and port number into the
"Destination" box, separated by a colon (for example,
webproxy.jtan.com:3128 to connect to JTAN's anonymizing WWW Proxy
server... or you can use port 3129 for transparent mode, port 3127 for aononymizing proxy in front of Tor, or port 9050 for pure Tor).
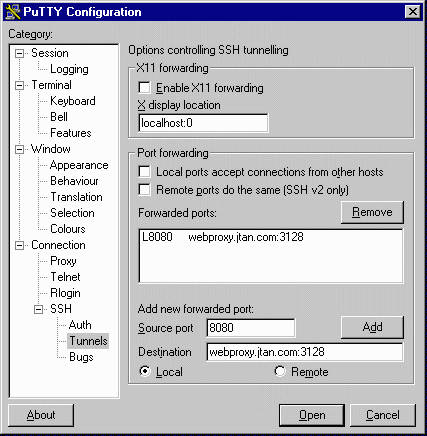
Now start your session and log in to your shell account. Be sure to select SSH and not Telnet. (Port forwarding will not be enabled until after you have logged in with SSH). Remember that your local end of the tunnel is on "localhost". So if you are setting up the WWW proxy, specify "localhost" as your proxy address, with the port number you chose at the local end (8080 in the example above). Here's an example of what the proxy config on MSIE 5.5 looks like when using a SSH tunnel.
To check that PuTTY has set up the port forwarding correctly, you can look at the PuTTY Event Log (see section 3.1.3.1). It should say something like this:
2001-12-05 17:22:10 Local port 3110 forwarding to
popserver.example.com:110
As long as you keep the shell connection open, the tunnel should remain
operational.
Reverse Tunneling with SSH
It's possible to set up an SSH tunnel to allow the outside world to connect into your PC. This is a little trickier, but it can be done. Such a tunnel is called a "remote" tunnel and uses the -R switch in OpenSSH. Be careful with remote tunneling as it can bypass firewall protection and expose your PC to remote attacks. For this reason, remote SSH tunnels are often restricted such that they can only be accessed on the remote machine.Using OpenVPN may be a better choice if you make extensive use
of reverse tunnels as OpenVPN tunnels are bidirectional by default.
Puncturing Firewalls that block Port 22
What if your firewall blocks port 22 on home.jtan.com? Not a problem.
Try using any of the unorthodox ports for
connecting to our server with SSH.
SOCKS4 with SSH
OpenSSH, including the Cygwin (www.cygwin.com) port for Windows, has the -D option which creates a SOCKS4 compatible forwarding service on the local host. Using this technique, you can forward one application or specific SOCKS compatible applications to follow the SSH tunnel while all other port 443, 80, etc. traffic continues to go out normally so you can easily access internal resources, etc. without setting up complicated routes. The command looks something like this:ssh -p 443 -D 8080 hostnameThen turn on the proxy options and select localhost and port 8080 for the application(s) that you would like to forward.
OpenVPN Setup
OpenVPN allows your PC to "tunnel" through the internet and appear as if its part of the JTAN LAN. Unlike SSH tunnels, OpenVPN will tunnel all ports and services through to JTAN: mail, web, dns, even ping! OpenVPN will assign a unique, public IP address to the other end of the tunnel, potentially allowing tunneled connections to be made in both directions. The bidirectional nature of OpenVPN tunnels can put your PC at risk. If you don't need the full VPN capability, you are probably better off with SSH port forwarding. In order to use OpenVPN, you need to download and install the 2.1 or later version OpenVPN client software. Note that 2.1 series features are required. The 2.0 version will not work. OpenVPN clients are available for Windows, Linux, BSD, and Mac OS X. Clients can be downloaded from the OpenVPN web site and other locations.Once you have OpenVPN installed, you will need the following client certificate files available from the JTAN Members Pages. Look for these files at the "JTAN Client Certs" link under Account Services, Misc, on the lower right.
- Your JTAN Client Certificate
- Your JTAN Client Private Key
- JTAN's VPN CA Certificate
Once these files are in place, you can start OpenVPN.
Windows users please note: In recent versions of Windows, you must run OpenVPN as Administrator!
Services | Resources | Contact | News | Members | Signup
| Copyright
© 1991-2014 JTAN All rights reserved All use of this site subject to terms. |